Cyber Yankee: The National Guard Just Simulated A Cyberattack That Brought Down Utilities Nationwide
National Guardsmen just completed a two-week training exercise which saw them respond to a simulated cyberattack that took out critical utilities across the United States called Cyber Yankee.
The exercises have become an annual event, but this year took on even more significance after coming on the heels of several major ransomware and cyber attacks that crippled large parts of American infrastructure in recent months.
The exercises were part of the seventh Cyber Yankee, an training event that brings together guardsmen from throughout the New England region to test their responses against simulated cyberattacks. This year’s exercises simulated a cyber attack that targeted utilities on the West Coast before spreading east across the United States towards New England. In addition to offering hands-on training on how to respond to active cyberattacks, the exercise was also intended to build cyber defense collaboration between the National Guard and private sector partners, the FBI, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, the Federal Energy Regulatory Commission, and U.S. Cyber Command, among others.
“We do it in an exercise environment so that when it does happen, we’ve already got those relationships established not just from a National Guard but from all of our critical infrastructure, our federal, local, state partners,” said Maj. Ryan Miler, state cyber operations officer for the Connecticut Army National Guard. “We’ve established those lines of communication and then it’s that much easier to get together and respond.”
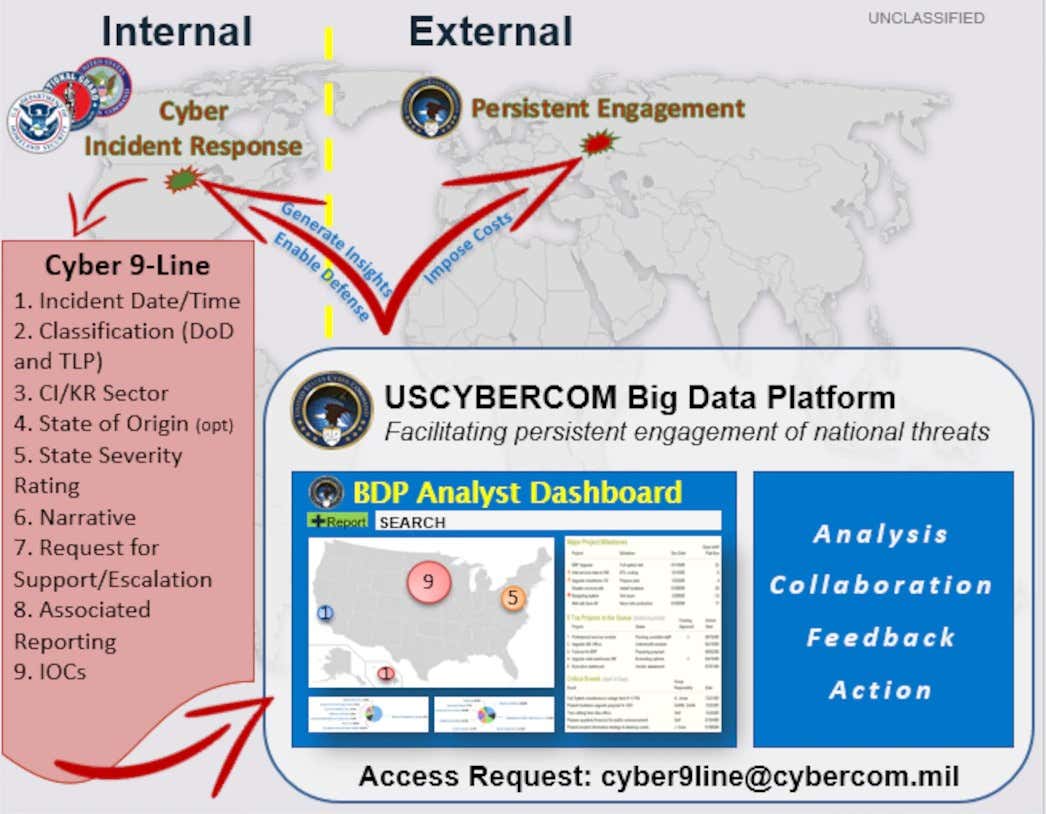
This year’s Cyber Yankee saw the annual exercise’s first use of the new Cyber 9-Line system developed by U.S. Cyber Command (USCYBERCOM). Cyber 9-Line offers National Guard cyber units a template of questions that allow them to quickly communicate the specifics of a suspected cyberattack up the chain of command to USCYBERCOM. Once CYBERCOM has that information from Cyber 9-Line, it can then more quickly and efficiently diagnose that attack and offer information back to the reporting unit, who can then share that intel among affected local governments and industry partners. “The Cyber 9-Line is still in its infancy, but after standing up this program a few months ago, we have already [seen an impact],” said U.S. Air Force Lt. Col. Jeff Pacini, CNMF Future Operations Deputy Chief in a USCYBERCOM press release last year. “Ultimately, the goal is to provide mutual support to each other.” The Cyber 9-Line questionnaire is similar to other nine-line formats used by U.S. armed forces for requests such as medical evacuation or close air support.
Lt. Col. Cameron Sprague, Chief Information Officer for the Connecticut Air National Guard and deputy exercise director for this year’s Cyber Yankee, said that the simulated cyberattacks were designed to be as realistic and complex as possible in order to prepare for the types of incidents becoming more and more common across the country:
It’s really hard to do an exercise like this effectively. Many cyber exercises involve activities that resemble a game of capture the flag, which are too easy and aren’t necessarily applicable to real-world crises. Operating effectively in incident response environment is really hard. That’s what a lot of teams first take away when they’re walking through this is how we’re actually going to do an incident response plan. That’s the big point of this.
Exercise leaders said that the teams conducting mock attacks offered the National Guard an opportunity to have a better idea what to expect in the event of actual cyber attacks and ransomware operations. If you know how your enemies conduct attacks, you can be better prepared to defend against them.
Last year’s Cyber Yankee exercises saw over 200 guardsmen come together to combat various cyber threats. The guardsmen were divided into four Blue Teams tasked with responding to simulated cyberattacks, a Red Cell which conducted those attacks, and a White Cell which “regulated and assessed event operations.”PUTIN SAYS “PATRIOTIC” RUSSIANS COULD HAVE BEEN BEHIND CYBERATTACKSBy Joseph TrevithickPosted in THE WAR ZONEARMY HIRES COMPANY TO DEVELOP CYBER DEFENSES FOR ITS STRYKERS AFTER THEY WERE HACKEDBy Joseph TrevithickPosted in THE WAR ZONERUSSIA MAY BE TESTING ITS GPS SPOOFING CAPABILITIES AROUND THE BLACK SEABy Tyler RogowayPosted in THE WAR ZONETOP RUSSIAN SUBMARINE DESIGN BUREAU HIT BY CYBER ATTACK WITH CHINESE CHARACTERISTICSBy Joseph TrevithickPosted in THE WAR ZONEPUTIN SAYS WHOEVER HAS THE BEST ARTIFICIAL INTELLIGENCE WILL RULE THE WORLDBy Joseph TrevithickPosted in THE WAR ZONE
U.S. Army Col. Woody Groton, who directed last year’s Cyber Yankee, said in 2020 that the exercise is designed to pit guardsmen against the same types of cyber threats currently faced by U.S.-based companies and infrastructure:
Cybersecurity, especially in critical infrastructure and state government, is a huge issue right now. You can see it in the news every day. Ransomware attacks are on the rise; loss of data, loss of intellectual property. It’s hard to keep up with the adversary. We’ve also, in the last several years, seen significant uptick in cyberattacks and attempted cyberattacks against the electrical industry and water. By training on this ahead of time, we’re better prepared in case of an actual incident.

Cyber attacks on civilian infrastructure have taken precedence as a national security concern in recent years as they have become more common and crippling. A ransomware attack shut down the United States’ largest fuel pipeline in May 2021, leading to fuel shortages on some parts of the East Coast. Officials for Georgia-based Colonial Pipeline eventually paid close to $5 million in ransom to end the cyberattack, of which the FBI was later able to recover some 85% in the form of cryptocurrency.
A similar ransomware cyberattack followed on the heels of the Colonial Pipeline attack in June 2021, this time against the world’s largest meat processing company. It’s not just large private sector entities who are under attack, however, as ransomware attacks against local governments and institutions are increasing at an alarming rate across the US. In one example, a National Guard unit in Louisiana thwarted a cyberattack on government offices in 2020 that was suspected to have originated from North Korea and possibly have been related to elections in that state.
While many of these attacks have been reported to have perpetrated by criminal organizations rather than state actors, many fingers have been pointed in the direction of the Russian government. Some attacks have even been presumed to have originated directly from Russian intelligence services, such as the 2020 cyberattack on the information technology management company SolarWinds which led to breaches of servers owned by U.S. government entities and private companies alike. Russia denied any involvement in that attack.

